The insatiable thirst customers have for higher amount of mobile data is growing tremendously.
The stats from Statista suggest that usage of mobile data has increased from 7 exabytes to 17 in a span of two years and will be almost 49 exabytes in 2021. The compound annual growth rate of the increase is about 47 percent. The everyday mobile activities like video calls, voice calls, social media usage and e-commerce are the key drivers behind this increased mobile traffic.
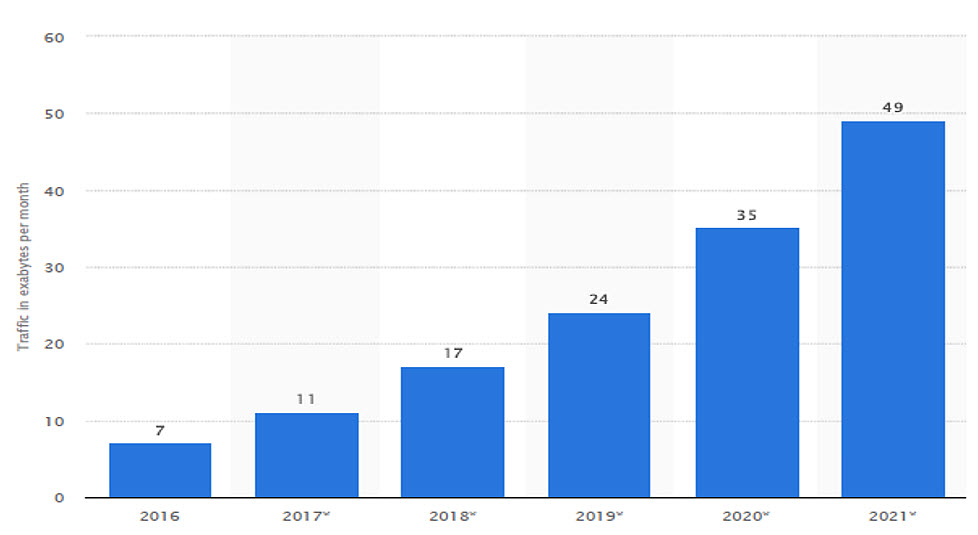
Telecom operators now face a massive increase in their network costs due to this data explosion. Stats also suggest that the cost for accessing and backhauling network will almost double in the next five years.
So, the big question now is how operators can manage this data explosion?
The answer lies in the effective implementation of ‘Network Optimization and Data Monetization.’
Focusing on these two parameters will enable operators to provide bandwidth in a more cost-efficient way and benefit from the expected rise in data. Here are some ways mobile operators can intelligently expand their network capacity and monetize data:
- Optimizing Video Delivery
An explosion of mobile video consumption is likely to drive the anticipated mobile data growth over the next few years. According to Cisco, mobile video will make up 78 per cent of all global mobile data traffic by 2021.
However, it is found that more than half of all video sessions are abandoned before the subscriber reaches midpoint. Accordingly, telco operators can reduce wasted bandwidth by closely matching the download to the playback speed (pacing) as opposed to downloading the full video.
- Intensifying Traffic Shaping
Traffic shaping can be used to prevent network congestion, alter user behaviour, and optimise monetization of data usage. Most operators are already using basic tools for steering user behaviour and limiting peak usage, either by rate-limiting after a certain download volume, implementing tariffs with usage caps, or time-based tariffs.
- Density Geographies
Congestion in network and scarcity of spectrum problems are different in diverse geographic locations. They apply to a small portion of the operator carriers’ coverage area. Carriers can set prices based on the regional realities of the data usage. Adopting the yield-management practices and driving requirement-based usage in underutilized areas improve profits.
- Quality and Traffic Prioritization
Customers who need a higher quality of service are willing to pay more for it. These segments can be targeted by MNOs to capture incremental value. This can be done by offering quality-of-service guarantees; thus, ‘prioritising’ premium traffic during times of potential network congestion.
- Time-of-Day Pricing
One of the greatest challenges for MNOs is ‘peak hours’. Just as some voice plans are known to have different charges for peak and off-peak periods (often lower rates at night), we can expect operators charge varying rates depending on the time of day by ‘de-averaging’ data pricing. A study by Nielson shows that mobile data usage on social apps is at their peak for four hours a day. So, the telco operators can adjust speed and charges according to the usage time.
Pricing by Data Type
Though differences in types of video usage give operators some flexibility, rising demand for data-heavy video will still be the biggest strain on most networks. This can be countered by plans that are priced by data type. For instance, offering unlimited internet and e-mail usage but pricing video traffic based on quantity consumed.
Stats from Android Central suggest that for an hour of HD video streaming more than 1 GB of data is used. As mobile video streaming has the largest growth rate of all mobile content categories, charges can be defined accordingly.
Conclusion:
With the enormous surge in mobile data, MNOs should have the capacity to monetize this traffic, yet to do so; they require unique visibility into the makeup and usage of the data itself. To gain such visibility, internet solutions can help them handle the data explosion more intelligently.
Managing data explosion is a big challenge but implementing the right broadband solutions will enable MNOs to close the revenue gap and increase profitability.

 s also include resources on their website, issue a press release, and make spokespeople available to the media.
s also include resources on their website, issue a press release, and make spokespeople available to the media.